Hackers Slam Tor Proxy Service Blaming Onion.top for Diverting Ransom Money
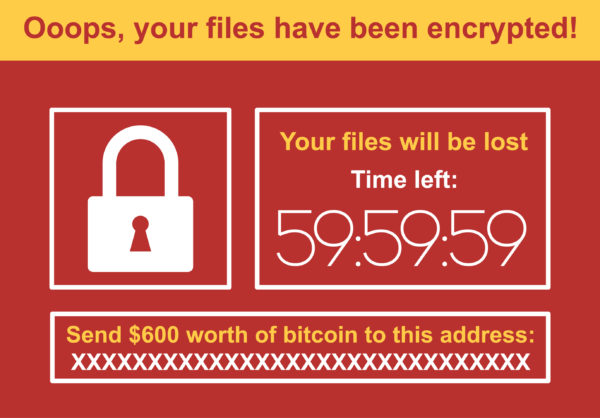
Hackers have often used ransomware software to extort money from businesses and individuals. First, they infect the system with a malware that encrypts the data files and documents, making it…