Idle Buddy Virus: A potential Ransomware
Idle buddy virus is a malicious executable file that is a part of IdleBuddy Application. In your hard disk, this file can be traced to C:\ Program Files (x86 folder)….
Idle buddy virus is a malicious executable file that is a part of IdleBuddy Application. In your hard disk, this file can be traced to C:\ Program Files (x86 folder)….

For British companies, ransomware attacks are becoming a virtual nightmare. The extent of ransomware shenanigans is also substantiated by the numbers mentioned in a report compiled by SonicWall, a company…
In a latest ransomware shenanigan, a production plant of Boeing has been attacked by WannaCry ransomware. According to local news reports, the aircraft manufacturing giant’s production plant of Charleston, South…
Over the weekend, the automated dispatch system of 911 in Baltimore sustained a cyber attack, which resulted into 17 hour shutdown of the automatic emergency services. Following the attack, Baltimore’s…

On the morning of 22nd march, majority of Atlanta’s municipal employees were sent home because the entire computer network of the city government was facing an unrevealed blackout. Later on, it…

We are all well aware of the threat posed by ransomware attacks for personal computers and handheld computing devices. But researches are pointing out towards another trend in near future…

In the previous blog, we have discussed some of the pointers highlighting how ransomware codes are being evolved amid all the technological innovations. Here, we will continue to carry forward…

In the cyber sphere, ransomware is a hot topic these days. From shenanigans of WannaCry in more than 150 countries to the virtual hostage situation of Atlanta, ransomware has become…

On the morning of March 22nd , majority of Atlanta’s municipal employees were sent home because the entire computer network of the city government was facing an unrevealed blackout. Later on,…
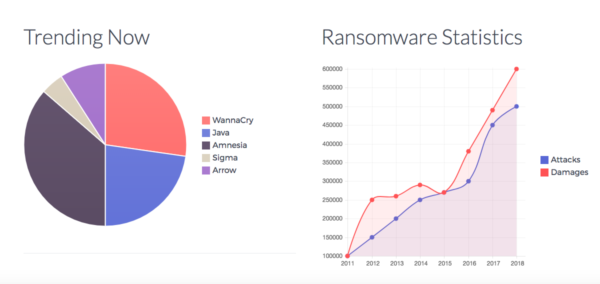
Ransomware has always been one of the most malicious computer viruses ever designed. Most ransomware packages operate by infecting the users’ PCs and locking them out of their files through…