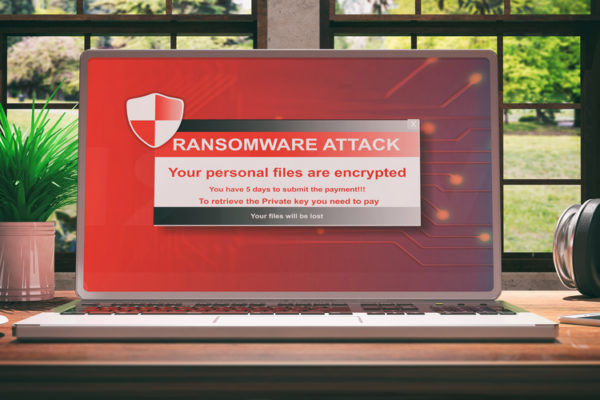
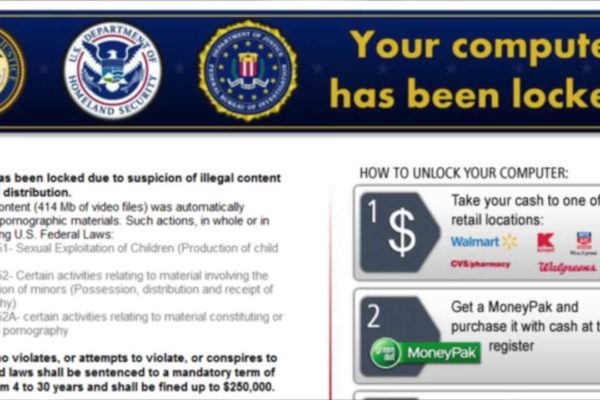
Hackers have caused “a catastrophic loss” time and time again by encrypting databases and locking out employees.
As Desiderius Erasmus once said “Prevention is better than cure”, organizations now follow a proactive rather than a reactive strategy. They tend to look first at the way malware works, with an aim to stop potential damage.
Ashley Wearne, General Manager for Security Software and Hardware Company Sophos, Australia and New Zealand, says that every day in his company’s labs, technicians witness about 500,000 new pieces of malware (short for malicious software). That is about half a million new pieces of malware detected every 24 hours, and only the tip of the cyber-iceberg.
Moreover, Wearne says that “18 months ago, malware was 80 per cent of the problem”:
“Now those 500,000 pieces of malware that we see every day represent just 14 per cent of all attacks. It’s staggering. The other 80 per cent is ransomware (a type of malware that encrypts data) and other types of attacks.”
Previously, the authorities served as the heavyweights and hackers were relatively easily to land a knockout punch. However, the cybercriminals learned to dodge the bullet. The business defenders punched hard and fast, but the cyber goons won rounds often.
Networking can be a blessing when it comes to sharing information with linked desktop and even wirelessly. However, with the threat of viruses prowling around, there has been a hurdle in businesses.
Wearne says that at first, these attacks were “annoyances driven by pimply teenagers doing something they thought was smart. Whereas now, these hackers or groups of people who are incredibly smart – some of the smartest people in the world using tools used by in National Security Agency US”
This makes tackling these threats extremely difficult.
The target-rich environment from Google homes and WIFI connected internet bulbs is an ideal situation for Hackers. Researchers at Gartner have predicted that by 2020, more than 25% of identified cyber-attacks in enterprises will involve the Internet of Things.
A technique in Artificial Intelligence (AI) notes down patterns that these hackers use for profiling their work and grouping cyber threats into easily recognizable batches. AI requires a lot of input of mass data, so that it can identify the good among bad.
AI has already identified about 27 techniques that developers of malware use to enter into a system. AI will recognize these techniques and put solutions in place before a damage is caused. These systems are quite smart and can recognize new learning patterns.
Therefore, rather than dealing with each threat individually (about 50,000 threats every day), a system recognizes one of the 27 techniques and puts a stop to it. The fight becomes intense with least of the system’s energy wasted on jabs and body blows. The software boxer now dodges every punch thrown at it. The opponents will still punch, but their efforts will be useless.