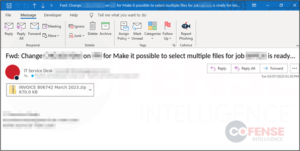
The Emotet botnet malware operation has returned to action following a three-month hiatus and is now infecting devices worldwide using emails that carry malicious ZIP attachments.
Emotet is an old (2014) banking trojan that evolved into a malware distributor in 2017, considered responsible for several high-profile attacks in the following year.
In 2019, it added the EternalBlue exploit that allowed it to spread rapidly on networks, but in January 2021, a coordinated international law enforcement operation severely disrupted it.
Emotet returned in November 2021 through another malware spreader botnet named Trickbot and has since gone through various phases of dormancy and activity, experimenting with various infection chains and multiple payloads.
As reported by Cofense, the current campaign uses emails that masquerade as invoices, containing Word documents of an inflated 500MB size to help evade detection by antivirus solutions that typically skip scanning such large files.
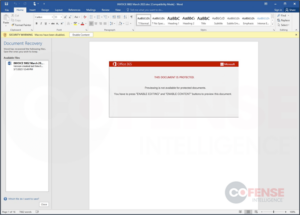
The documents load malicious macros on the victim’s Microsoft Office software to download a DLL, which is the Emotet loader from compromised sites that enjoy a good reputation and are more likely to evade AV detection.
This final payload also has an inflated size of 526MB, using garbage (unused) data and padding for the same detection evasion reasons.
After Emotet is loaded on the breached device, it will run in the background and await commands from the C2 (command and control) server. Analysts discovered several new C2 IP addresses that support the newest spamming wave.
Apart from commands, Emotet can also fetch, decrypt, and load additional payloads on compromised systems, most notably ransomware.
Gateway to ransomware
Recently, Europol announced a successful operation that resulted in tracking down two core members of the DoppelPaymer ransomware gang in Germany and Ukraine.
DoppelPaymer is no longer active, but its operation between 2019 and 2021 has resulted in multi-million damages. Europol reports that U.S.-based victims paid at least $42,000,000 in ransoms to the DopperPaymer gang, which doesn’t include the cost sustained from business disruption, reputation damage, legal coverage, etc.
In the same report, Europol revealed that many of these catastrophic DoppelPaymer attacks were enabled by Emotet, which introduced the data-encrypting payload after breaching valuable networks.
How to protect from Emotet
The threat arrives via email, so a key security measure is to remain vigilant and avoid downloading attachments of unsolicited messages sent by unknown contacts. Frequent email security training plays a crucial role in helping organizations deal with threats like Emotet.
Also, while Microsoft now blocks the execution of VBA scripts and macro code hiding inside malicious documents by default on Office, if you’re working on an environment that requires keeping that feature active, you should avoid opening document files outside a sandboxed environment.
Network administrators should also block all IP addresses known to be parts of the Emotet infrastructure or associated with its distribution, including those shared by Max Malyutin on Twitter.
In the instance that a device has fallen victim to the Emotet botnet malware or any other Trojan malware capable of fetching, decrypting, and loading additional payloads, including ransomware, on compromised systems, it is imperative to seek assistance from a reputable and professional ransomware removal and recovery company. One such company is Monster Cloud, which specializes in removing ransomware attacks and recovering encrypted data. With a team of highly skilled security experts, Monster Cloud provides a comprehensive solution to ransomware problems, guaranteeing the complete removal of the threat and the recovery of critical data. Utilizing the services of Monster Cloud allows for individuals and organizations to regain control of their infected devices and safeguard against future attacks.
