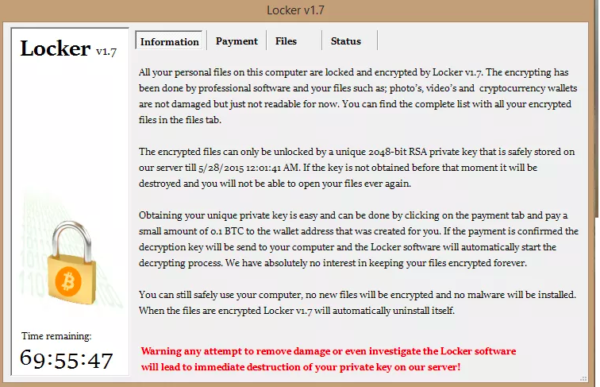
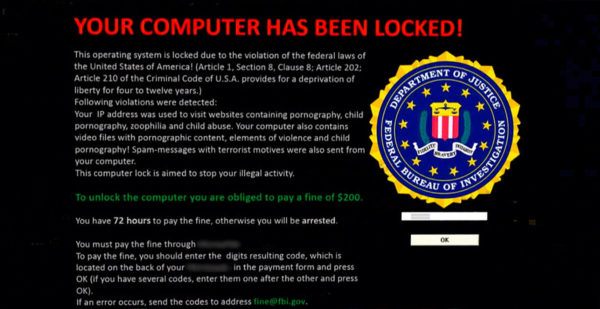
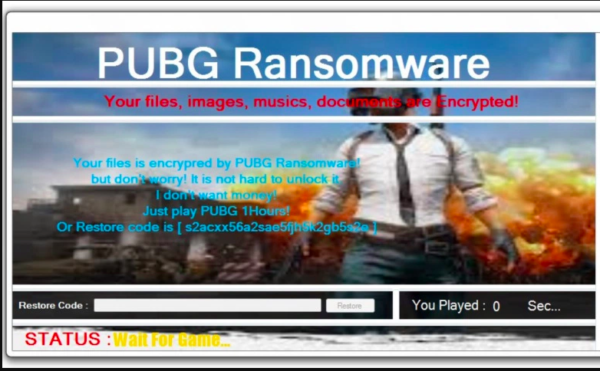
Manufacturing Systems are Next in Line to Bear the Brunt of Ransomware Attacks

Ransomware attacks are constantly evolving with time. We have seen how they have shifted their spotlight to local government bodies in the last couple of months. Millions of dollars have…