Scammers Stole money From Ransomware Virus Attackers

Hackers and cyber attackers have always been a problem for the online community, since the inception of the internet. Most hackers attack a website with the intent to cause damage…

Hackers and cyber attackers have always been a problem for the online community, since the inception of the internet. Most hackers attack a website with the intent to cause damage…
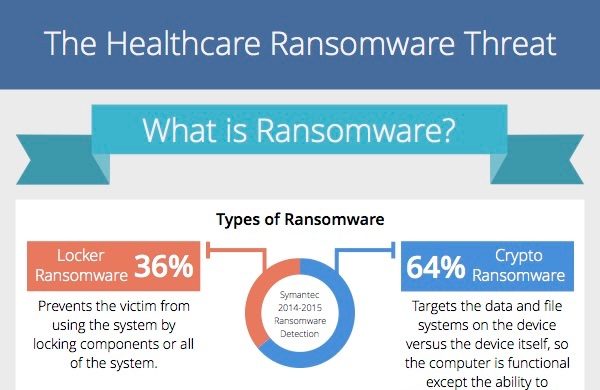
Healthcare is a precarious industry on its own. It represents one of the cornerstones of any society as the health and well-being of citizens depends squarely upon this. With that…

Just recently Google announced the launch of its newest version in the Chrome series, Google Chrome 65. The newest version for the browser comes with 45 security fixes, blocking of…

Ransomware is one of the most repulsive aspects of modern programming and computing. It relies on slimy and unethical practices which enables the programs to engage in activities to extort…

Ransomware removal is important for users who find themselves in a position where they’ve become a victim of the widely used antics by hackers online to affect the PC’s of…

Unlike normal attempts where UDP packets containing random information are attacked this group of hackers is leaving messages for ransom in these packets. The group has a very unique demand…

A latest computer virus that is being studied by analysts has attacked and crashed over 1,000 cash registers at Tim Hortons donuts and coffee fast food restaurants during the week….

Security researchers that have a keen eye on ransomwares and malwares have recently discovered another new malware strain that has the abilities to detect when users copy addresses from a…

Marquis de Sade put it most elegantly when he said, “All, all is theft, all is unceasing and rigorous competition in nature; the desire to make off with the substance…

A new research was carried out over nearly 1 million Ethereum accounts , which has led to the discovery that 34,200 smart contracts are in a vulnerable position ready to…