Ransomware turns attention to government agencies
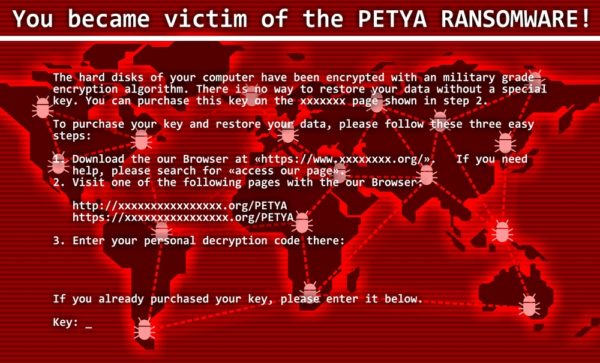
Ransomware shot to headlines back in 2015 after it began targeting a number of businesses and then demanding ransoms in exchange for decrypting their data. It not only shocked businesses…

Ransomware shot to headlines back in 2015 after it began targeting a number of businesses and then demanding ransoms in exchange for decrypting their data. It not only shocked businesses…
Ransomware has been a huge problem for businesses and domestic homes alike. They’ve come in various forms over the past 3-4 years and have caused major incidents where public data…

Ransomware attacks continue to affect organizational networks regardless of their size. In addition, enterprises that work in public domain have become the favorite target of ransomware operators. In a recent…
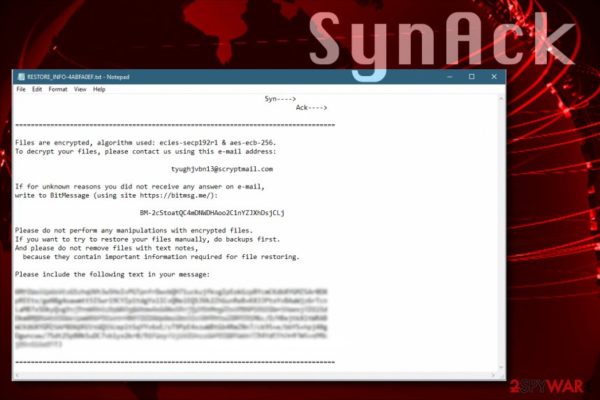
There is a reason why ransomware continues to be a leading cyber threat. The cryptovirological operators are constantly working to make their attacks more lethal, deadly and unassailable against ransomware…
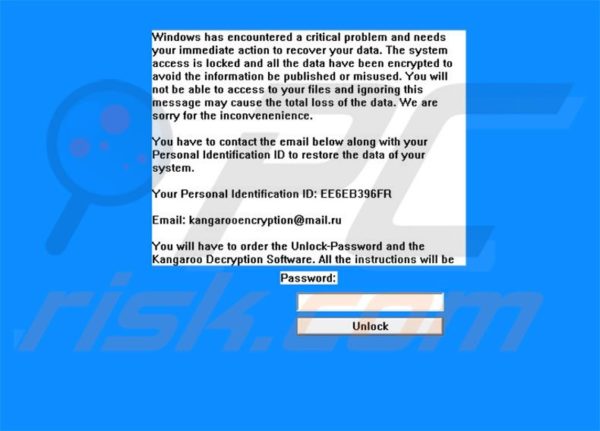
At the core of it, ransomware attack is intended to play out like any ransom activity where perpetrators scare victims into paying the extortion money. In cryptovirological attacks, the perpetrators…
It seems that even Ukrainians have gotten used the fact that no matter which ransomware removal tools their Energy Ministry uses, it’ll end up being the subject to another ransomware…

The years of 2016 and 2017 had a lot of tech related developments. A lot of new innovations and concepts began their foray into the public imagination. However, there was…
Ransomware attacks are growing at an exponential pace. Majority of them are real cryptographic malware programs that lock down the files on the affected device and you need ransomware repairs…

This is the last blog of this series where we will talk about some protective measures against cryptovirological attacks. In this series, we have already covered different types of ransomware…
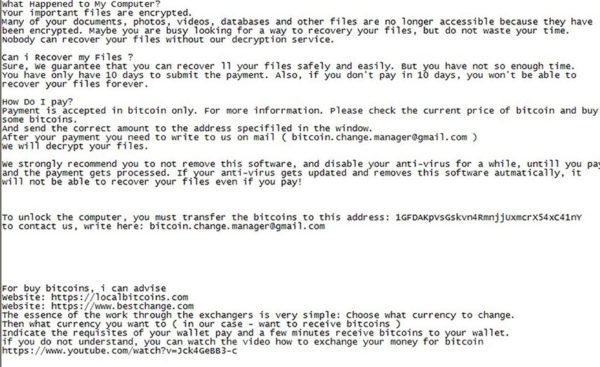
AutoTRON is relatively a new ransomware strain on the block. It is locking down the files on the affected device through Advanced Encryption Standard (AES) module. It is able to…