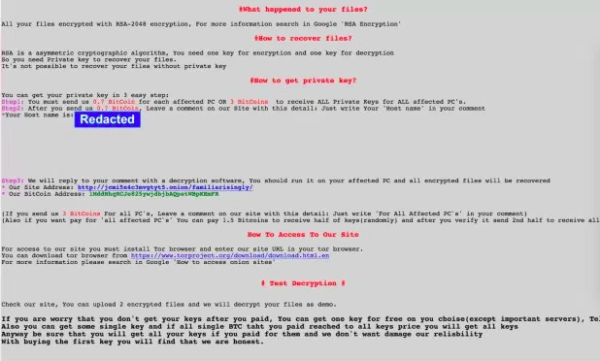
Quant Loader Trojan- a Successful Ransomware-as-a-service Product
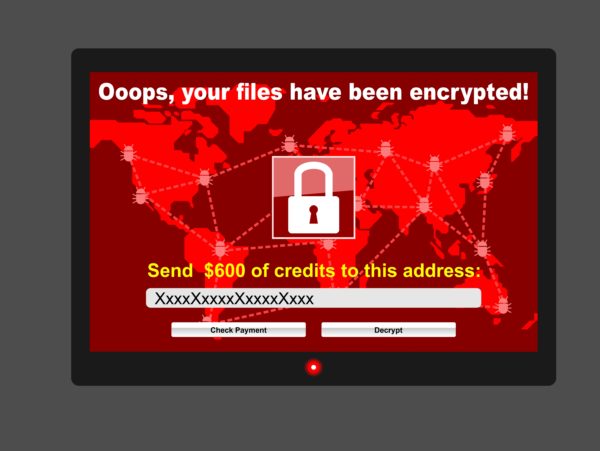
Trojans are very efficient exploitation tools of the digital domain. Innumerable cyber attacks have been carried out through digital Trojan horses in all those years. With time, the development of…