Ransomware 101: Locker Ransomware
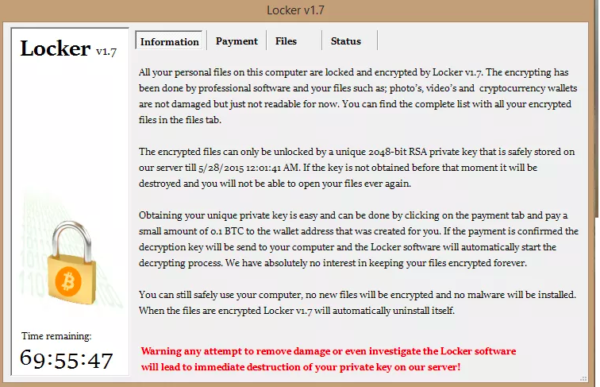
Ransomware has been around as a potent cyber threat for years now. But still many people, particularly the ones who are the potential target of ransomware operators, are not very…

Ransomware has been around as a potent cyber threat for years now. But still many people, particularly the ones who are the potential target of ransomware operators, are not very…

There is a reason why ransomware has become a leading cyber threat of today. The infection of these ransomware strains is effective because once they start their encryption activity, it…
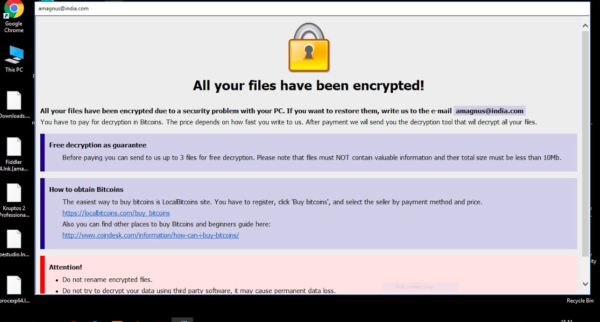
To streamline their ransomware removal measures, cyber security folks are constantly hunting for new strains on the cyberspace. Lately, a group of them have discovered another variant of Dharma/Crysis. The…

Many times before, we have discussed about the changing preferences of ransomware operators. If we specifically review the ransomware attacks in this year, it is quite apparent that cryptovirological cybercriminals…

Gandcrab ransomware was first detected at the start of this year. From then on, this ransomware strain has become one of the most active cryptovirological scripts on the web. According…
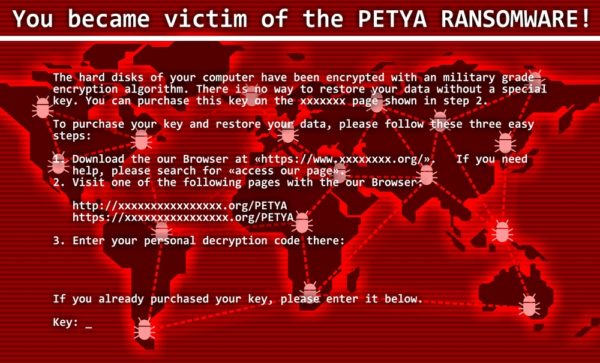
Ransomware shot to headlines back in 2015 after it began targeting a number of businesses and then demanding ransoms in exchange for decrypting their data. It not only shocked businesses…
Ransomware has been a huge problem for businesses and domestic homes alike. They’ve come in various forms over the past 3-4 years and have caused major incidents where public data…

Ransomware attacks continue to affect organizational networks regardless of their size. In addition, enterprises that work in public domain have become the favorite target of ransomware operators. In a recent…
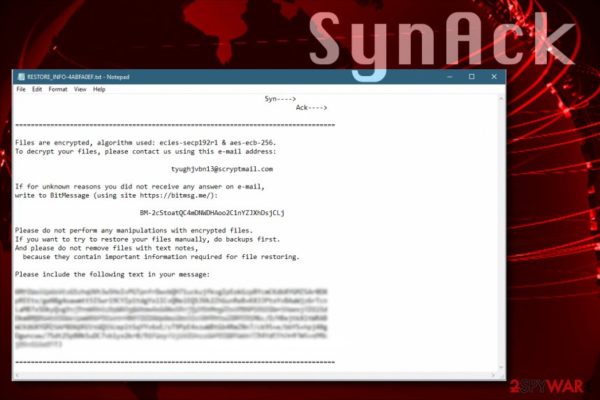
There is a reason why ransomware continues to be a leading cyber threat. The cryptovirological operators are constantly working to make their attacks more lethal, deadly and unassailable against ransomware…
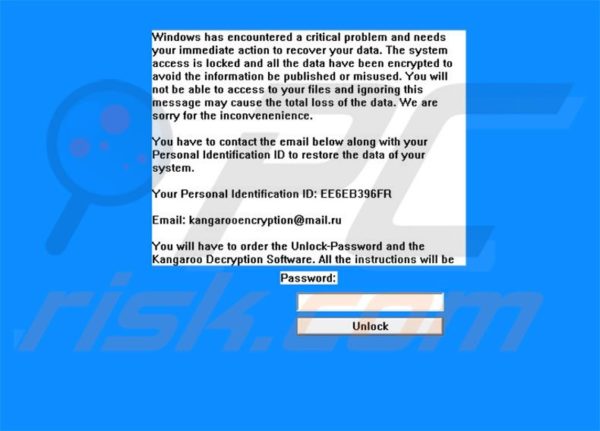
At the core of it, ransomware attack is intended to play out like any ransom activity where perpetrators scare victims into paying the extortion money. In cryptovirological attacks, the perpetrators…